Utilizing Google Dorks For Hacking
Google is the most popular look for motor on the world-wide-web suitable now. Persons use it to discover their answers, photos, films, news, notes, etc. But, did you know that Google can also assistance hackers to come across susceptible targets and steal unauthorized information and facts?. Google is as much handy for hackers as any other general consumer.
Hackers use the Google search engine to obtain Vulnerable systems (Be it a databases, web-site, stability cameras, or any IoT gadget) with the aid of some unique lookup queries. There are many Google lookup engine queries that can uncover vulnerable systems and/or sensitive information and facts disclosures. These queries are recognized as Google Dorks.
Notice: This posting is only for instructional purposes. You can use this knowledge to maximize your system’s protection or for any moral function.
What is Google Dork or Google Dorking?
In 2002, Johnny Extended started to collect exciting Google lookup queries that uncovered susceptible programs or sensitive facts disclosures. He labeled them Google dorks. Some persons call it Google hacking.
Google Dorking is the system for discovering susceptible targets making use of Google dorks. Google Dorking can return usernames and passwords, electronic mail lists, sensitive paperwork, and website vulnerabilities.
Ethical Hackers use Google Dorking to strengthen process security. Black hat hackers use this approach for illegal activities, which include cyber terrorism, industrial espionage, and identity theft.
Google dorks can locate Footholds, Sensitive Directories, Vulnerable Documents, Vulnerable Servers, Community or Vulnerability Details, Many On line Equipment, Documents Made up of Usernames and Passwords, Delicate On-line Purchasing Data and Pages That contains Login Portals.
List of Google Dork Queries (Up to date List)
Google dork Queries are exclusive look for queries that can be searched as any other query you lookup on the Google lookup motor. You just require to sort the query in the Google research motor along with the specified parameters.
1. Google Dorks For Hacking internet websites
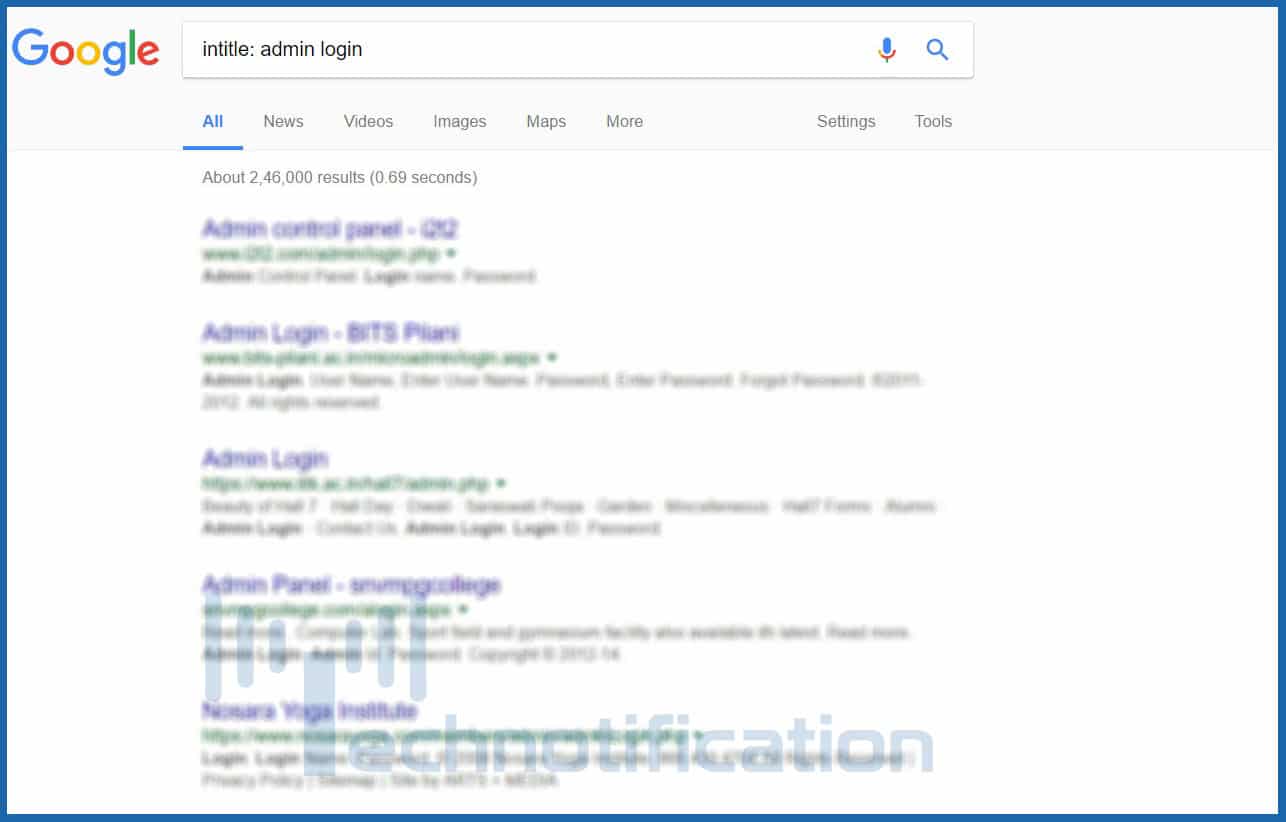
- intitle: This dork will convey to Google to clearly show only all those webpages that have the time period in their HTML title. For example: intitle:”login page” will present individuals webpages which have the time period “login page” in the title text.
- allintitle: It is identical to intitle but looks for all the specified terms in the title. For illustration: allintitle:”login page”
- inurl: It queries for the specified phrase in the URL. For example inurl:”login.php” and inurl:proftpdpasswd
- allinurl: It is very similar to inurl but seems for all the specified conditions in the URL. For example: allinurl:”login.php”.
- define: Google will define this message and will search for what experienced this mistake. For example: outline:”sql syntax error”
- website: This dork will return all the web pages of a particular site that is crawled by Google. For instance, web page:technotification.com.
- hyperlink: It will also seem in the site for URLs that maybe are vulnerable to SQL injection. For case in point: website link:index.php?id=
2. Google Dorks For Hacking Files
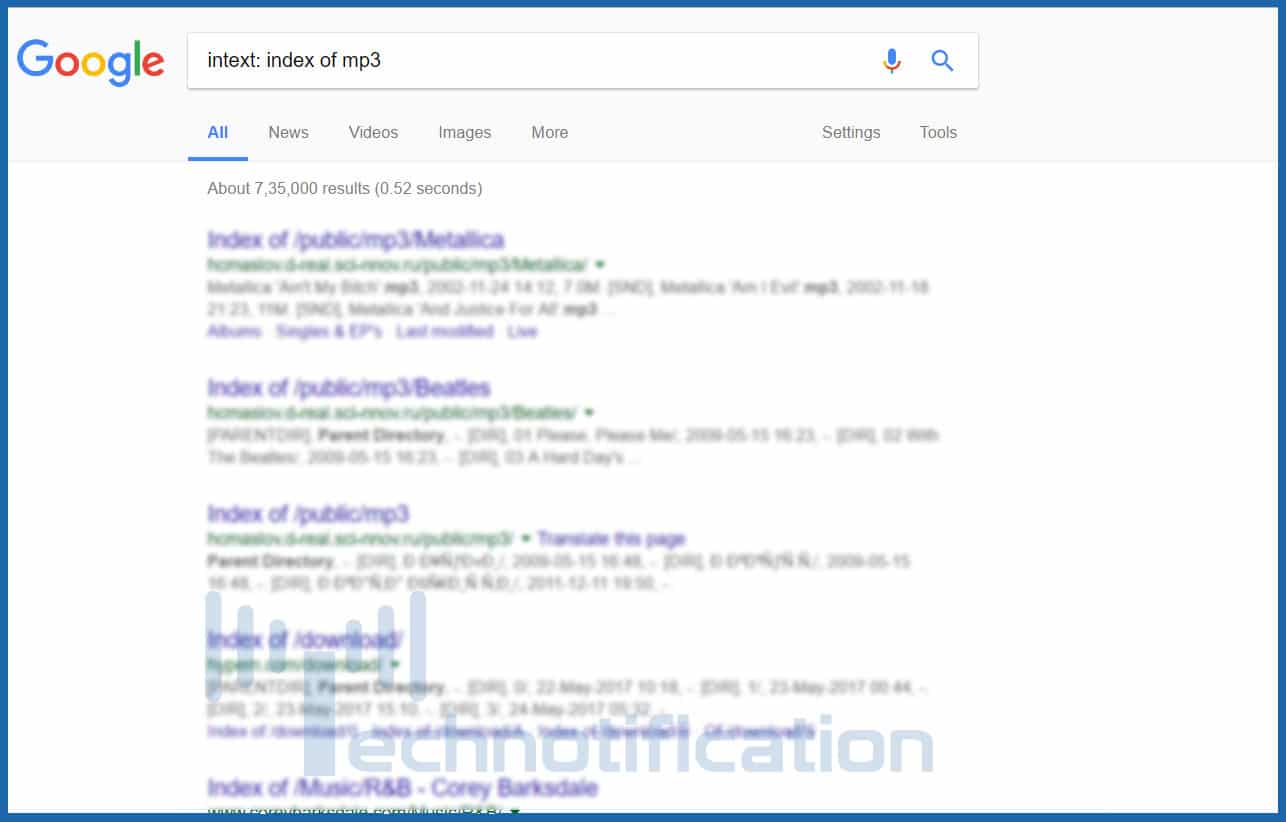
- filetype: Searches for distinct file varieties. filetype:pdf will seem for pdf information in internet websites. filetype:txt appears to be for data files with .txt extension. This way you can look for for a file with any extension like mp4, mp3, Mkv, and many others. internet site:onedrive.live.com shared by
- intitle: You can glance into file directories of sites directly and download specified file intitle: index of mp3 for mp3 information. You can exchange mp3 with any other extension. You can also use to find any distinct film or video game. intitle: “index of ” intext: “movie name” .
- e-book: uncover any book utilizing Google search engine. for illustration e-book: java
3. Google Dorks for obtaining username and passwords
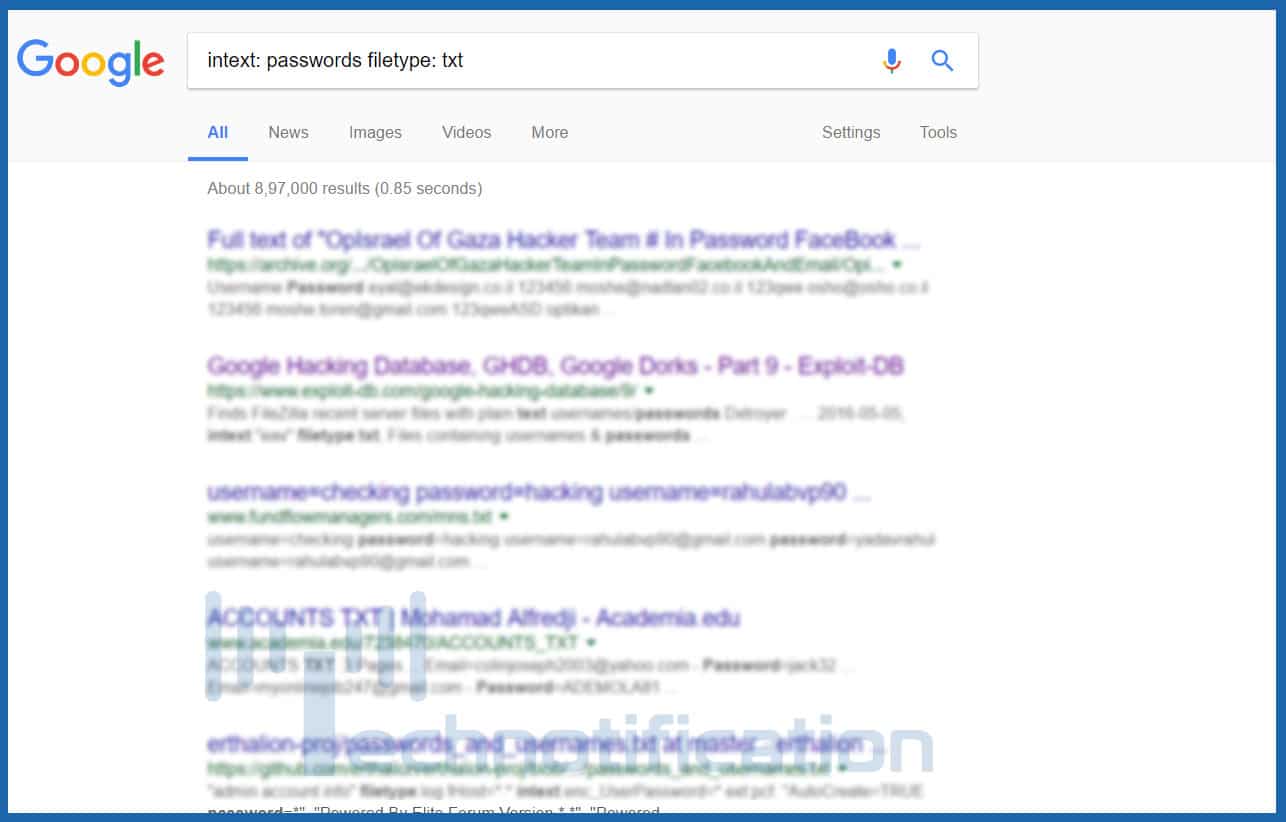
- intext: passwords filetype: txt
- mysql historical past data files
- intext: account aspects filetype: txt
- intitle:index.of intext:”secring .skr”|&q…
- people.lst
- passwd
- learn.passwd
- pwd.db
- htpasswd / htpasswd.bak
- htpasswd / htgroup
- spwd.db / passwd
- passwd / and so on (responsible)
- config.php
- passlist
4. Google Dorks For Hacking Protection Cameras
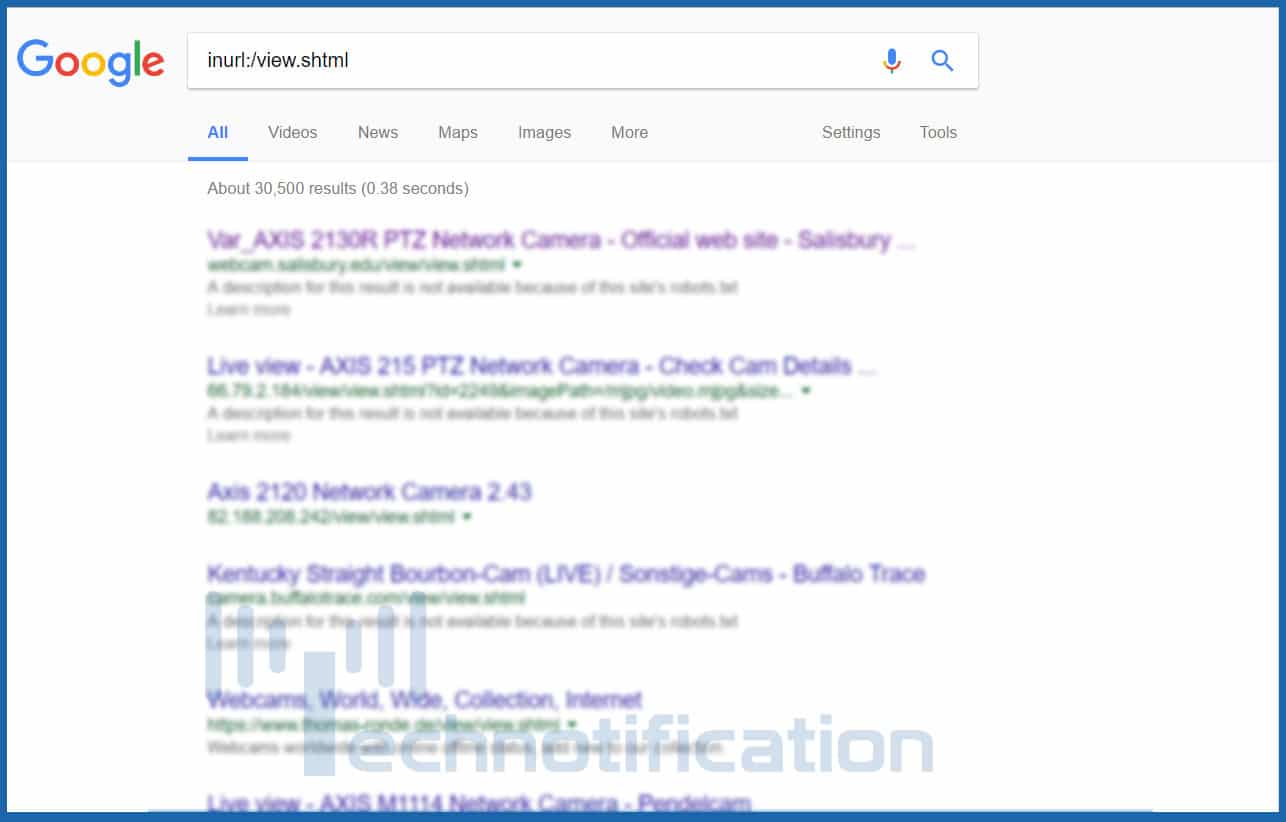
Style any of these queries into google to uncover vulnerable stability cameras
- Inurl:”CgiStart?webpage=”
- inurl:/perspective.shtml
- intitle:”Live Look at / – AXIS
- inurl:perspective/look at.shtml
- inurl:ViewerFrame?Manner=
- inurl:ViewerFrame?Manner=Refresh
- inurl:axis-cgi/jpg
- inurl:axis-cgi/mjpg (movement-JPEG) (disconnected)
- inurl:view/indexFrame.shtml
- inurl:watch/index.shtml
- inurl:check out/check out.shtml
- liveapplet
- intitle:”live view” intitle:axis
- intitle:liveapplet
- allintitle:”Network Camera NetworkCamera” (disconnected)
- intitle:axis intitle:”video server”
- intitle:liveapplet inurl:LvAppl
- intitle:”EvoCam” inurl:”webcam.html”
- intitle:”Live NetSnap Cam-Server feed”
- intitle:”Live Check out / – AXIS”
- inurl:indexFrame.shtml Axis
These are the most popular research queries utilised by the hackers. Nonetheless, there is a major databases of such queries available at HackersForCharity identified as Google Hacking Database. You can obtain more google dorks in this databases.
